Endpoint Protection
When looking at different types of cybersecurity protection for your business, which of the following is the right endpoint security strategy for your business: antivirus (AV) software or endpoint protection and response (EDR)? These tools might seem similar at first glance, but choosing the wrong one could compromise the security of your data and, ultimately, your business.
That is why you need something to protect your business and while both cybersecurity tools overlap, they are not the same. Understanding the differences between AV and EDR can improve the cybersecurity posture of your company.
So what strategy should you use when securing your organization’s endpoints? We’ll break it down for you to get a better sense of which is most appropriate for you.
To start, all software has a signature, a unique identifying feature. Antivirus detects the presence of malicious software by identifying its unique signature and checking it against a database of known malware. This is why it’s so important to keep antivirus software updated. In a single day, over 100,000 new malicious signatures can be added to an antivirus database alone!
Antivirus Software
Antivirus works by scanning a device for malware such as worms, trojans, adware, ransomware, and others. It accomplished this by using:
- Signature detection to monitor for evidence of known threats and block them from taking further action
- Heuristic analysis to examine new programs for suspicious code by comparing it to malicious signatures from a database
- Integrity checks to inspect system files for evidence of corruption
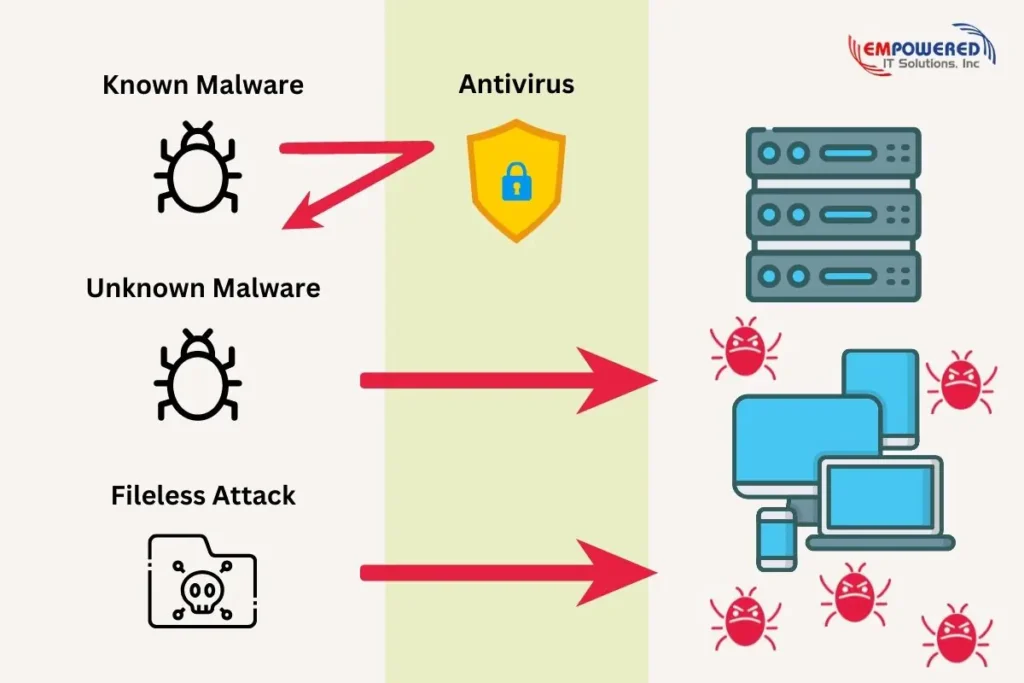
Identifying malicious software’s ID is important but not enough to identify and handle new sophisticated cyber threats that end users are faced with. Modern malware is advanced enough to change its signature so additional capabilities are needed to identify malicious behavior happening in computers, servers, and networks.
In order to identify malicious behavior, we need more information about the activity taking place. When did the activity begin, where did the activity occur, and how far was its reach?
To combat next-generation malware, we need to shift from traditional signature-based protection to behavior-based profiling.
Behavioral analysis lessens the dependency on signature-based detection and moves toward the behavior of software running on your devices or network. This is where EDR comes int, Artificial Intelligence is built into the EDR agent running on your device to enable quick decision-making and action.
The added threat intelligence provides the tools to find and understand threats better. It gives us forensic evidence to understand what happened, how it happened, and the depth of the impact.
Endpoint Detection & Response
EDR protection creates a multi-layered security system that includes antivirus tools along with the most advanced threat prevention:
- Machine learning that supports behavioral analysis to monitor beyond known threats to prevent unknown and fileless malware in addition to common signature-based attacks
- Collection and analysis of data from across a network to stop, remove, and trace an attack
- Advanced threat intelligence and threat hunting to actively mitigate network attacks before they can cause significant damage
- In some cases, EDR can roll back the systems/data to their state prior to the malware attack, eliminating corruption or even data encryption from a ransomware attack
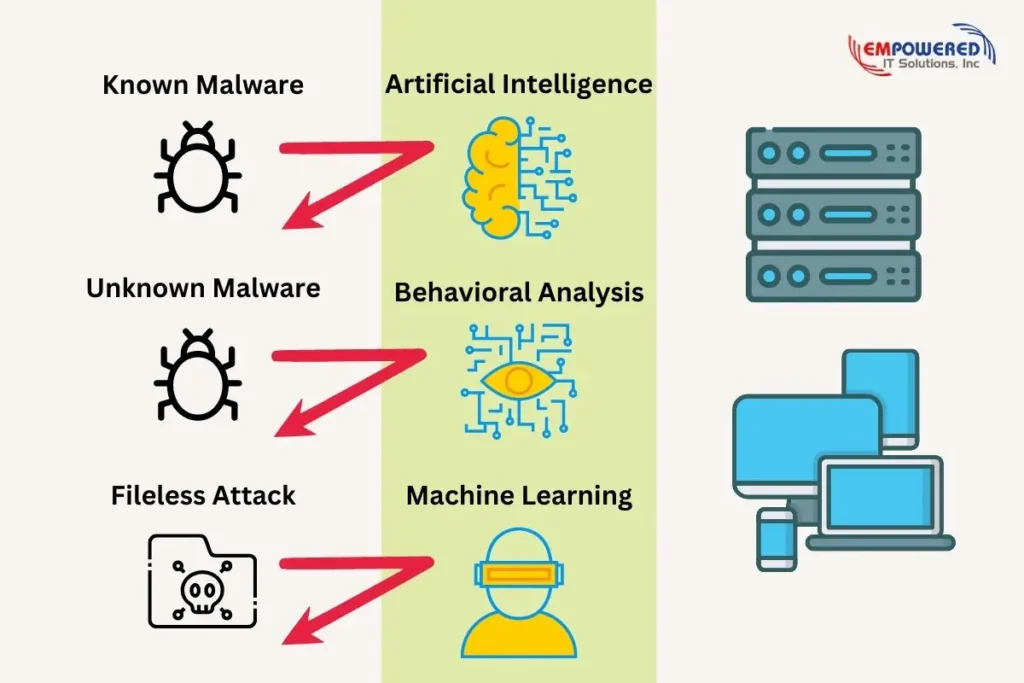
Antivirus software is suitable as a bare-minimum option for small businesses, but anyone working with sensitive data should invest in stronger endpoint protection. It’s always more cost-effective to prevent an attack from happening than it is to clean up and recover after one. Make sure the endpoint security you employ is appropriate for your business needs.
To learn more about the power of endpoint protection schedule a call with one of our experts.
