Secure Your Business: The Importance of Cloud Security
Businesses are increasingly turning to cloud services for their agility, scalability, and cost-efficiency. According to Gartner, cloud services will soon constitute more than half of IT spending within the next three years. As businesses embrace cloud computing, it’s crucial to prioritize cloud security to protect sensitive data and ensure business continuity.
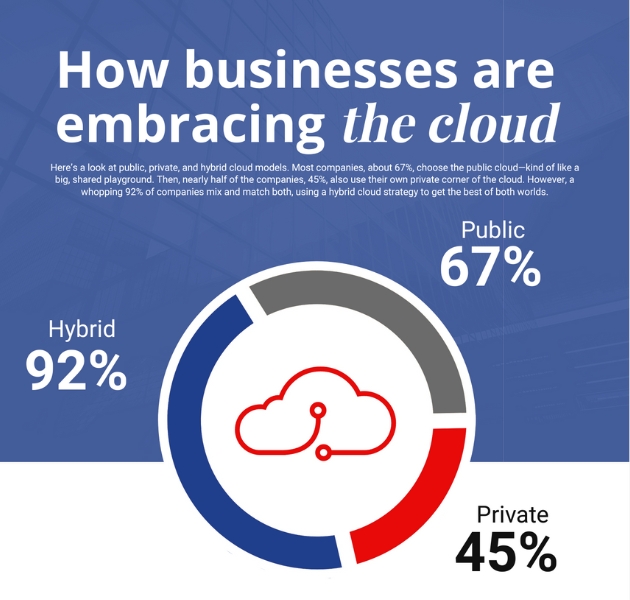
Understanding Cloud Security
Cloud security encompasses the technologies, policies, controls, and services that protect cloud data, applications, and infrastructure from threats. With 92% of companies adopting a hybrid cloud strategy, it’s essential to implement robust security measures to address both public and private cloud environments.
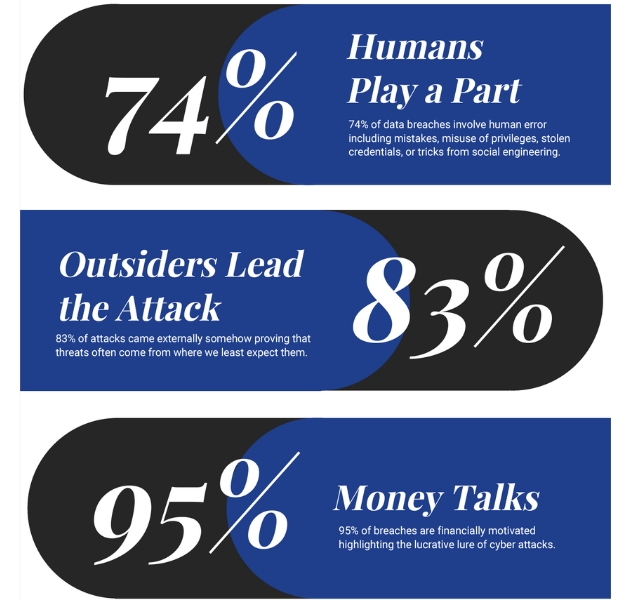
The Human Element in Cloud Security
Human error remains a significant factor in cloud security breaches, contributing to 74% of data breaches. These errors include misconfigurations, misuse of privileges, stolen credentials, and social engineering attacks. Ensuring comprehensive training and awareness programs for employees can mitigate these risks.
Key Pillars of Cloud Security
1. Data Security
•Data Encryption: Encrypting data both in transit and at rest ensures that even if data is intercepted or accessed without authorization, it remains unreadable.
•Data Classification and Key Management: Classifying data based on sensitivity and managing encryption keys effectively enhances data protection.
•Data Loss Prevention (DLP): Implementing DLP technologies prevents unauthorized data transfers and potential breaches.
2. Identity & Access Management (IAM)
•Multi-Factor Authentication (MFA): Adding an extra layer of security beyond passwords significantly reduces unauthorized access.
•Strong Password Policies and Least Privilege Principle: Enforcing complex passwords and granting minimal access rights necessary for tasks minimizes risks.
•User Provisioning & Access Reviews: Regularly reviewing user access ensures that permissions are up-to-date and relevant.
3. Incident Response
•Incident Detection and Analysis: Early detection and thorough analysis of security incidents help mitigate impacts swiftly.
•Incident Containment and Eradication: Prompt containment and removal of threats prevent further damage.
•Business Continuity and Disaster Recovery (BCDR): Having a robust BCDR plan ensures that business operations can continue with minimal disruption.
•Post-Incident Review: Analyzing incidents post-occurrence helps improve future response strategies.
4. Infrastructure Security
•Network Security and Vulnerability Management: Securing the network and continuously scanning for vulnerabilities helps protect against external and internal threats.
•Patch Management and Security Configuration Management: Regularly updating software and configuring systems securely prevent exploitation of known vulnerabilities.
5. Governance & Compliance
•Policies and Procedures: Establishing clear security policies and procedures ensures consistency and adherence to best practices.
•Awareness and Training: Regular training keeps employees informed about the latest security threats and how to respond.
•Cloud Security Audits and Regulatory Compliance: Conducting audits and ensuring compliance with regulations protect against legal and financial repercussions.
Why Cloud Security is Crucial
Cloud security is essential for protecting sensitive data, maintaining customer trust, and ensuring business continuity. Financially motivated cyberattacks account for 95% of breaches, highlighting the lucrative nature of exploiting insecure systems. With 83% of attacks originating from external sources, robust cloud security measures are more important than ever.
Create a Culture of Security
To further strengthen your overall digital security, it’s essential to create a culture where everyone understands the importance of keeping data secure. Download our comprehensive checklist to help your organization build and maintain robust security practices. This checklist includes actionable steps and best practices to ensure your team is well-prepared to handle security challenges.
Starting your cloud journey with a security-first mindset is critical for navigating today’s evolving threats. Partnering with a trusted provider like Empowered IT Solutions strengthens your defenses and guides you through digital transformation securely.
