Your business has been forced to turn to a number of security solutions to mitigate the cyberthreats that have grown exponentially both in number and sophistication. These solutions generate high volumes of threat data that need to be monitored and quickly acted upon to prevent an incident from occurring. Is this something your business struggles with? This is where our Security Operation Center comes into play.
What Is a Security Operations Center?
A security operation center or SOC is a command center that houses highly skilled security personnel, processes, and technologies to continuously monitor and analyze cybersecurity activity while preventing, detecting, and responding to incidents.
It is comprised of security analysts and engineers who oversee security operations. The key benefit of having a SOC as part of your security team is the improvement of incident detection through continuous monitoring and analysis of data activity.
The team looks for variations and anomalies in the systems they monitor through a security information and event management system or (SIEM) and use it for incident response, threat hunting, intrusion detection, and risk management.
What Happens in a Security Operations Center?
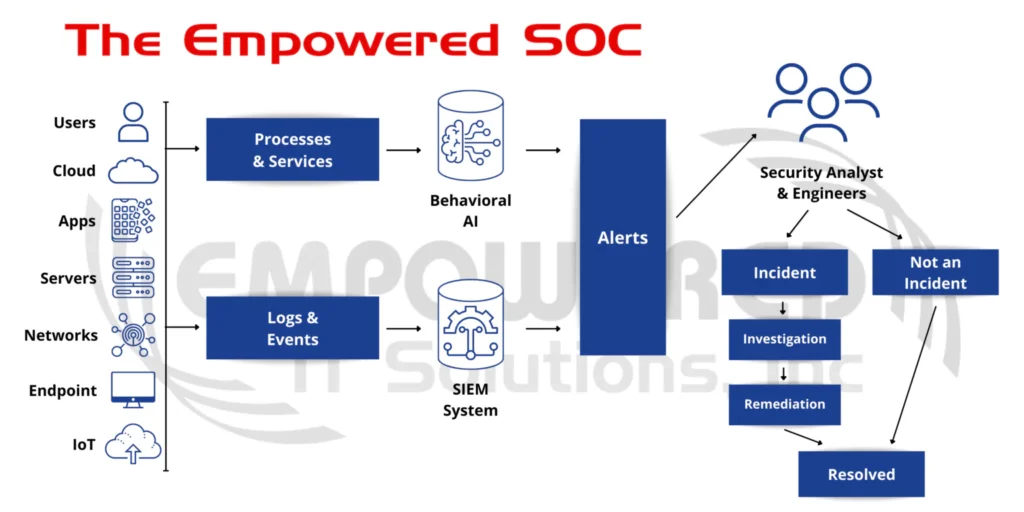
First, we have data collected from logs and events that are triggered by users, applications, endpoints, and any system/device being monitored. This data is collected and run through a real-time correlation engine to generate alerts for the team to investigate. Those real-time alerts are passed on to monitoring team to do an initial triage to understand context, relevance, importance, and priority. This is done to truly understand if there’s an incident at hand. If it’s a simple and straightforward issue, the analysts work on resolving it quickly.
If an incident is found, it is passed on to our investigation team for further analysis. A further detailed level of investigation is carried out on these alerts to ascertain the importance, relevance, impact, and user involvement. The team goes through the data in a wider and deeper approach to understand all aspects and elements (actors, attackers, indicators, and the blast radius to see how far it goes). The team then creates a plan of action to resolve the incident with the least impact and greatest efficiency where it will then be carried out and then the incident can be closed.
What are the Benefits of a SOC?
You might have the top-of-the-line endpoint/network protection, but who will manage it? the SOC deciphers the logs and alerts coming from the security systems, identifies a probable incident and the type of response needed to eliminate any threat.
Incident response
This team of cybersecurity experts operate around the clock to monitor, detect, and respond to alerts and incidents.
Rapid analysis
To facilitate the appropriate response threat intelligence feeds and security tools are used to quickly detect threats and fully understand incidents.
Reduce cybersecurity costs
An outsourced team of experts enables immediate access to talented cybersecurity professionals.
Reduce the complexity of investigations
Investigations are streamlined by having a dedicated team that can coordinate data and information from multiple sources.
The Empowered SOC
Our Security Operations Center (SOC) provides 24×7 threat monitoring, mitigation, and remediation services. They provide the analysis, monitoring, and threat intelligence needed to define how to protect against cyber-attacks across endpoints and networks. Our SOC identifies threats and ensures our customers meet regulatory requirements through a fully integrated range of response and remediation capabilities, keeping client systems and data, safe and available, at all times.
When a critical alert is received, the SOC coordinates with the Empowered IT local security support team to further investigate the threat and if it is determined to be malicious, immediate action is taken to ensure there is no impact on the client’s operations.
Furthermore, our SOC is intimately integrated with the Network Operation Center (NOC) and the Disaster Recover (DR) Team creating a 24×7 synergy. Just imagine that an incident was detected and stopped but it caused a corruption on one of your servers. Our SOC will coordinate with the server expert within the NOC for the server troubleshoot process, and if needed, the NOC expert with coordinate with the DR expert to recover a healthy version of the piece that was corrupted. All three experts working together aiming for the same goal: bringing back normal business operations as fast as possible. Now, to put it into perspective, if those three key functions are taken by three different providers, the synergy is lost with probable challenges for communication, “finger-pointing”, delays, among others.
We provide a SOC that can keep your cybersecurity perimeter constantly updated against new and evolving threats, 24×7.
